Protecting Employee Data

It's a typical Monday morning at a bustling tech company. Employees arrive, ready to give their best and contribute to the success of the organization. They trust that their company is doing the same, working hard to protect their personal information and to ensure a secure work environment. The company demands these types of morals and values from their employees, so, surely, they should reciprocate. Right? Unfortunately for the employees, today won't be a good day. Today the tangled web of IT systems used to provide corporate services will show the final signs of neglect, encumbered by years of inadequate operating budgets, lack of management willpower to improve, a growing amount of technical debt, and the penetrating effect of opaque 3rd party providers failing to meet their commitments.
BREACH!
The employees responsible for those corporate systems are in freefall, running around as fast as they can perform incident response processes that haven't been tested in years. Other employees hear about the effects of the breach, often in real time with information being released/shared publicly by reporters and whatever you call people who post on X. Even when information is provided, it is often hard to determine the actual effects, and what one can actually do about it.
With companies relying heavily on technology to manage their workforce, the amount of sensitive information they collect has skyrocketed. We're talking about personal details, payroll information, performance reviews, and even biometric data. If this information isn't handled properly, it can lead to serious problems like legal issues, damage to the company's reputation, and a loss of trust from employees. And that is just from the company angle. The damage to the individuals about whom the data refers can be way, way worse.
The News
These scenarios aren't just hypothetical. While the details vary, employee data is a valuable target. In November 2024, Amazon confirmed that a significant breach had exposed 2.8 million lines of employee data through a vulnerability in the MOVEit Transfer system.
The exposed Amazon dataset includes employee work contact information, email addresses, desk phone numbers, and building locations. While Amazon spokesperson Adam Montgomery confirmed the breach, he emphasized in a statement to TechCrunch that core Amazon and Amazon Web Services, or AWS, systems remained secure.
In late December 2024, Carruth Compliance Consulting, a retirement plan administrator for several Oregon school districts, experienced a significant data breach. This breach exposed sensitive information of thousands of current and former school employees across multiple districts.
Oregon-based third-party retirement plan administrator Carruth Compliance Consulting had information from more than 40,000 public school teachers and employees in California, Illinois, New York, Oregon, and Pennsylvania exfiltrated following a December attack by the newly emergent Skira Team hacking group, which purported the theft of data from 36 public schools across the U.S., according to The Record, a news site by cybersecurity firm Recorded Future.
In October 2023, the British Library experienced a significant cyber-attack orchestrated by the hacker group Rhysida. The attackers encrypted and destroyed much of the Library's server estate, compromising approximately 600GB of files, including personal data of Library users and staff. When the Library refused to pay the ransom, the stolen data was auctioned and subsequently dumped on the dark web.
The criminal gang responsible for the attack copied and exfiltrated (illegally removed) some 600GB of files, including personal data of Library users and staff. When it became clear that no ransom would be paid, this data was put up for auction and subsequently dumped on the dark web. Our Corporate Information Management Unit is conducting a detailed review of the material included in the data-dump, and where sensitive material is identified they are contacting the individuals affected with advice and support.
The Data Security Lifecycle and Corporate Responsibilities
There are two good documents to use when looking at data security. The first is the data security lifecycle and the Fair Information Principles(FIPP). Let's try and mash them together to get a picture (however incomplete) of how corporations should be thinking about employee data.
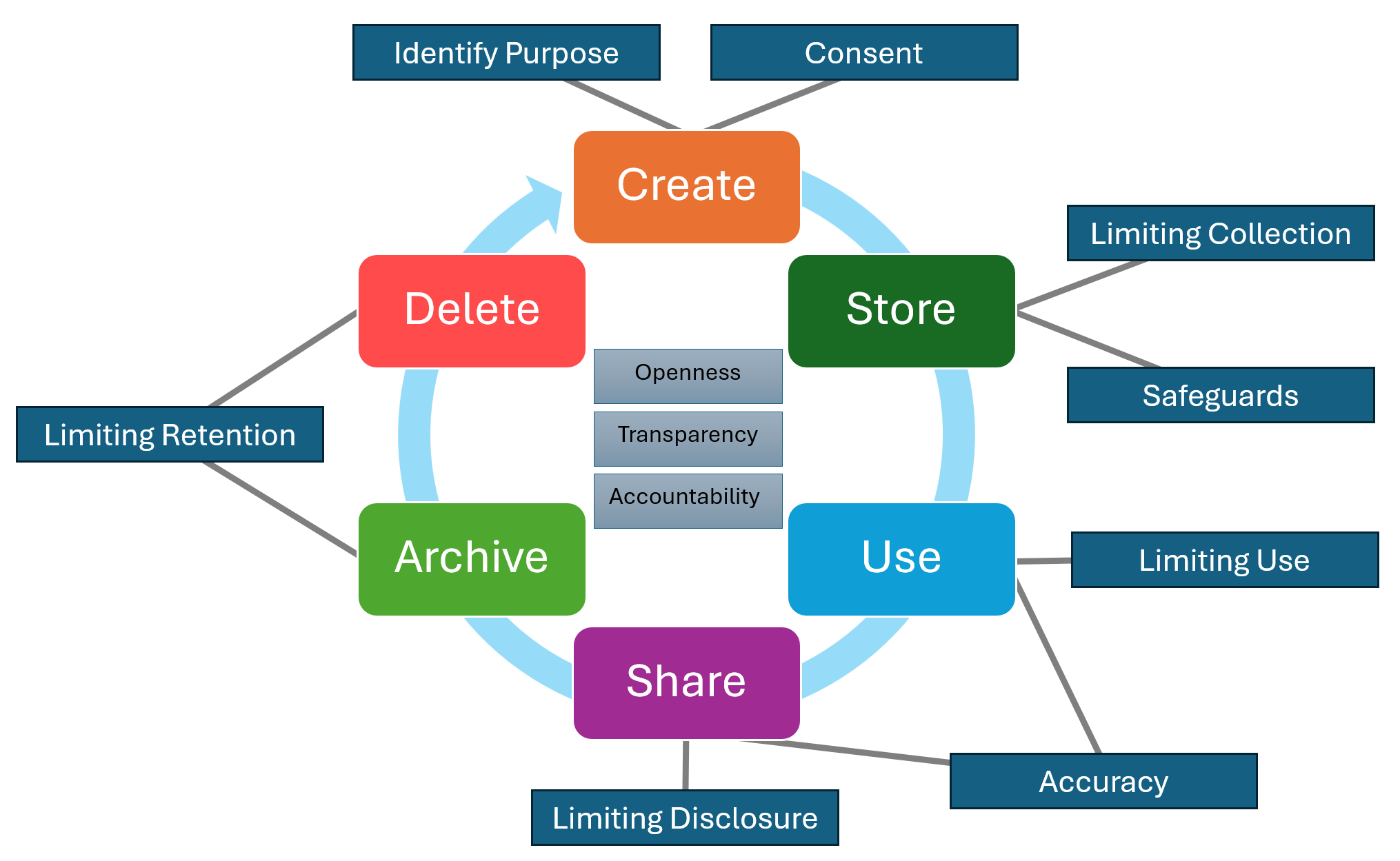
Create
This phase of the data lifecycle focuses on creation of data itself. An easy way to think about this is when a manager decides to hire an employee, and sends in a request to have the employee account created. At this point, data about the employee has been created, but it hasn't necessarily been "stored" in an active system for use.
From a FIPP perspective, employers should:
- Ensure data minimization by only capturing the amount of data that is necessary for the specified purpose
- Ensure data is of high quality and integrity (read: is accurate)
Store
Storing data is the act of making the collected data "live" or "accessible" within the system. An example here is that a request can go into a service desk to create a user, but until the user is created within the system (read: stored) the user object isn't actually usable. In modern organizations, this may actually be the act of storing user data in several systems required to conduct business (HR systems, finance systems, productivity systems, licensing systems, etc).
From a FIPP perspective, employers should:
- Implement appropriate security measures to protect data within those target systems (or where the data is stored)
- Maintain records of data storage practices and targets along with ensuring compliance to security policy of those systems
Use
Simply put, when data is viewed, processed or otherwise utilized in various activities.
From a FIPP perspective, employers should:
- Involve employees in the use of their data and seek informed consent where applicable
- Ensure data used is accurate, relevant, and timely
Share
Using data and sharing data can be considered synonymous, but they are effectively different concepts. Sharing data involves the exchange of data between different parties. An easy way to think about this is when I send employee data to a 3rd party payment processor responsible for issuing paychecks.
From a FIPP perspective, employers should:
- Clearly inform employees about how their data will be shared, with whom, and for what benefit
- Monitor and document data sharing practices and performance, ensuring compliance with corporate privacy and security policies
Archive
Effectively, archive is the act of pulling data out of active use and, potentially, entering the data into long-term retention systems (for example, for regulatory purposes). For example, an employee may leave the company but the company still has regulatory reasons to retain various records about the employee (even though no active changes should be permitted to those records).
From a FIPP perspective, employers should:
- Archive only the data necessary for long term retention
- Implement measures to protect this data from unauthorized access and breaches
Destroy
Effectively, data that is permanently destroyed using physical or digital measures (such as cryptoshredding).
From a FIPP perspective, employers should:
- Ensure data destruction policies/practices are effective and tested
- Document data destruction practices and ensure compliance with policies
Canadian Guidance
Individuals have a right to privacy at work, even if they are on their employer's premises and/or using their employer's equipment.
That is the first line in a Office Of the Privacy Commissioner Of Canada publication on Privacy in the Workplace. The publication aims to provide some guidance to employers on their responsibility to respect employee privacy and works to establish the line between the need to capture information about employees and the violation of their rights.
The article gives eight practical tips for employers:
- Examine all relevant legal obligations and authorities
- Map out what employee information is being collected, used, and disclosed
- Conduct Privacy Impact Assessments
- Test your proposed employee management information practices
- Limit Collection
- Be transparent and open
- Respect key privacy principles
- Be aware of inappropriate practices/no-go zones
Buried in the document is an interesting link to the PIPEDA Findings # 2022-006 which is a case about a company installing, without consent, audio/video recording devices in company vehicles.
We found that the System was not implemented for an appropriate purpose, in the circumstances. We accepted that Trimac had a legitimate need for implementing the System, including to ensure road safety, and that the System was likely to be effective in achieving those objectives. However, Trimac could have achieved the same ends in a less privacy intrusive way. Further, the loss of privacy resulting from Trimac’s implementation of the System was not proportional to the benefits Trimac hoped to gain. We consequently recommended that Trimac: (i) limit the audio functionality capabilities of the System to be active only when a driver is on-duty and/or driving; and (ii) technologically limit access to the personal information captured by the System to only those employees who “need to know” for Trimac’s purposes. Trimac agreed to implement all our recommendations such that we find this aspect of the complaint to be well-founded and conditionally resolved.
It is interesting to see PIPEDA used in these circumstances, and stresses the importance of the 4th partical tip defined above, testing the proposed employee management information practices. It was the finding of the privacy commissioner that the goals of the employer surveillence program could have been better achieved to strike a balance between employee and employer concerns.
Conclusion
In conclusion, while there may be limited direct legislation compelling companies to protect employee data, there are still mechanisms for employees to have their voices heard. Employees can raise concerns through internal channels, seek guidance from privacy commissioners, or even take legal action if their privacy rights are violated. It is ultimately in the best interest of companies to respect the rights of their employees, fostering a culture of trust and transparency that benefits everyone.
As data breaches become more frequent, the excuses of neglecting IT systems are increasingly unacceptable. Companies must prioritize robust cybersecurity measures to protect sensitive information and prevent breaches. This proactive approach not only mitigates risks but also demonstrates a commitment to responsible data management.
Interestingly, informed consent is crucial, even in the employer-employee relationship. Employers should clearly communicate how employee data will be used and provide alternatives if individuals decline to have their data shared with third parties (especially given the number of these 3rd parties that have suffered breaches). This practice respects employee autonomy and builds a foundation of mutual trust.
By adopting these strategies, organizations can create a resilient and trustworthy workplace that values privacy and security. Protecting employee data is not just a legal obligation but a fundamental aspect of ethical business practices that contribute to a positive organizational culture.

Member discussion